The Domain Name System (DNS) is an essential part of how the Internet works. It allows computers to talk to one another and enables us to use human-friendly URLs rather than memorizing IP addresses for our favorite sites. And as such an important part of the Internet, you can be sure that DNS is a prime target for hackers.
By disabling a single system, an attacker can take down a disproportionately large part of the Internet. In this piece, we discuss what DNS is, how it can be attacked, and why DNS servers can benefit from defenses like DDoS Protection and DNSSEC.
What is DNS?
The Internet functions a lot like the real-world mail system. With traditional mail, we label envelopes with a street address and expect them to be delivered to the right point on the globe. On the Internet, we type in a domain (like www.google.com) and expect to be connected to the correct webserver. In traditional mail, it’s the job of the postal system to ensure that our letters make it to the right place. When you send a letter, you write down a name, address, and postal code; however, you expect it to be delivered to a specific set of GPS coordinates on the globe.
That address that you write on the letter is essentially meaningless – it doesn’t intrinsically describe some point on the globe. The post office keeps look-up tables that allow them to identify the mapping from any street address on Earth to the corresponding location, post office, route, etc.
DNS servers provide the same service to you on the Internet. When you type in a URL, your computer doesn’t know where to send it. However, it does know who to ask: a DNS server. DNS servers are set up in a hierarchy, so that finding the IP address of www.google.com requires asking the com and google.com webservers.
This makes it easy to find any address in existence, since the owner of a site manages DNS requests for their site and are pointed to by the next DNS server up the chain. This service of resolving domains to IP addresses is crucial to the functioning of the Internet and make DNS servers a valuable target for hackers.
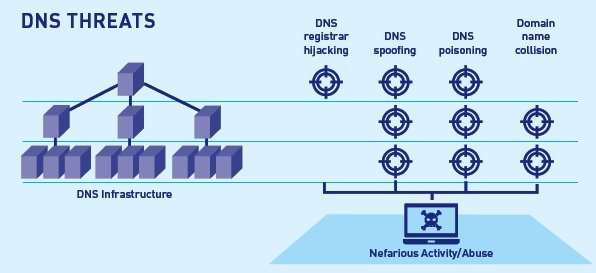
Threats to DNS
When attacking a DNS server, there are two main possible goals for an attacker. They can either make the DNS server inaccessible to users (disabling it) or ensure that it provides the incorrect IP address when someone asks for a given domain (spoofing it).
- Disabling
The first possibility for an attacker targeting a DNS server is disabling it. Most computers are configured to use a certain mail server for resolving domains to IP addresses. If that DNS server is unavailable, these computers are unable to access any site on the Internet where they don’t already know the IP address unless they find an alternative DNS server. In some cases (i.e. particular websites), only one DNS server may exist, meaning that disabling it would make it impossible for anyone to visit the site.
The simplest way to disable a DNS server is through a Distributed Denial of Service (DDoS) attack. An attacker with control of several different machines uses them to exhaust the resources of the DNS server, making it unavailable to legitimate users.
In October 2016, the Dyn, a major DNS provider, was the victim of a large DDoS attack. A botnet of between 50,000 and 100,000 IoT devices was used to launch the attack, which took over a thousand of the domains under Dyn’s control offline (including Amazon, Etsy, and Twitter).
Protecting against DDoS attacks requires state-of-the-art anti-DDoS services. The Dyn attack occurred against 20 different targets simultaneously and managed to disrupt services globally. Organizations need to deploy DDoS protection with massive scrubbing capabilities in order to protect against attacks at this scale.
- Spoofing
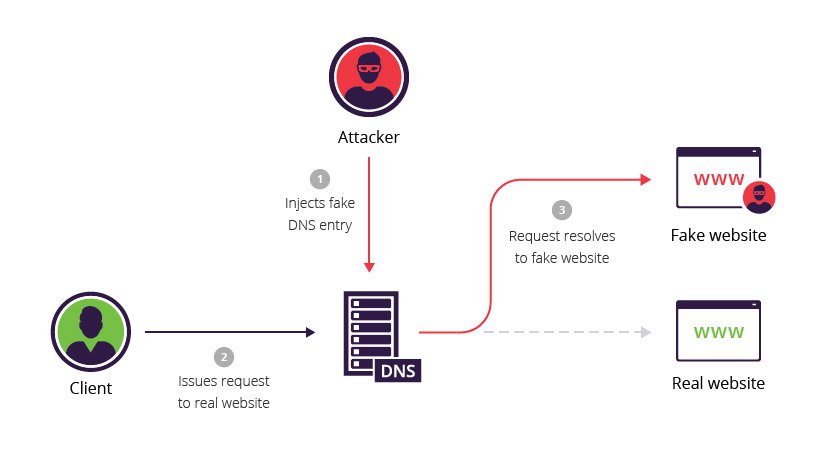
The other main threat regarding DNS servers is that an attacker may try to manipulate the lookup process. A DNS server is considered the final authority on the IP address that matches up to a given domain. If the DNS server has the wrong information, any computer that trusts it will go to the wrong webserver when resolving a request.
Using DNS cache poisoning or DNS spoofing, an attacker can cause this to happen deliberately. If an attacker compromises a trusted DNS server or convinces people to trust a malicious one, they can cause people to be redirected to a malicious site when requesting a legitimate one.
This is how the Great Firewall of China works and how it accidentally migrated overseas in 2010, blocking access to sites like Twitter in the US. One ISP accidentally set their DNS servers to China’s “poisoned” ones and others updated their lookup tables from this DNS server in a chain that eventually reached the US before it was corrected.
The Internet Engineering Task Force (IETF) is working on the problem of spoofed DNS records. DNS Security Extensions (DNSSEC) is an extension to the DNS protocol that requires DNS records to be digitally signed. If a record is not correctly signed (i.e. if it’s spoofed), users that utilize DNSSEC will detect the modification and reject it.
Ensuring a Secure Web
Properly functioning DNS servers are essential to a secure, functional Internet. By deploying protections like anti-DDoS systems and DNSSEC, an organization can diminish the probability of their DNS servers being disabled or of falling for spoofed DNS records.