Encryption vs Tokenization – which is better? While most firms have heard of encryption, tokenization is still a popular buzzword, and legacy security systems may feel uncertain about shifting to a new form of protection.
Every business leader knows how important it is to keep your data secure. Even as we see big-name brands like Marriot and British Airways suffer from significant data breaches, fewer than 30% of businesses are taking advantage of encryption. And the verdict is still out on tokenization – although it’s likely this newer tech isn’t faring any better.
Both encryption and tokenization can be integrated into your existing systems. And both focus on turning sensitive data into a cipher or code so that the original information is not recognizable. Each of these systems are also compliant-friendly. So you can use either own to achieve PCI DSS compliance.
But what’s the difference between the two? Surely every business should have at least one form of concealing their sensitive data from the prying eyes of hackers.
The key difference lies in how each system is set up.
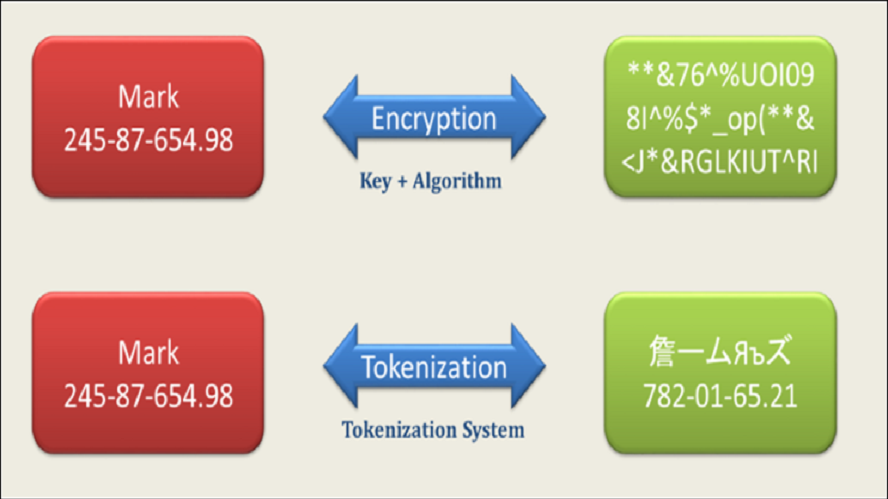
What is Encryption?
Encryption is when you use a private key to make data unreadable by those without that key. It has been the most common form of protection for years, and is used to safeguard all kinds of data. Payment Card Information (PCI), personal data, and credit card information are just some examples of what encryption is commonly used for.
What is Tokenization?
Tokenization is a form of data security where the data is replaced by an alphanumeric code. Unlike encryption, tokenization does not use a key. To decipher a token, you need the tokenization software that created the token itself.
Encryption vs Tokenization
So as we can see, encryption and tokenization are two similar but very different approaches to data security. And while both are acceptable forms of compliance when it comes to PCI DSS, SOC 2, and other data security standards, it’s safe to say that they also have differing levels of security.
Which is more hackable?
As you may have guessed, encryption is more hackable. All you need is the private key to break the encryption. Essentially, encrypted data can be reverse-engineered, which makes encrypted systems good targets for seasoned hackers.
Tokens can also be hacked, but only through middle-man attacks. Generally, this happens when a user gives sensitive information to a third-party, who can then use this information to access the original data. Usually this is an unintentional leak, but occasionally these breaches can be malicious.
We can see then that tokenization is a bit safer than encryption. Tokens are randomized, and since there is no pattern, it’s impossible to decipher them without having access to the original tokenization system. And the only way a hacker is going to get the data behind the token is if they can access the original data directly.
Which is more compliance friendly?
Overall, tokenization is more compliant than encryption, although both methods are still accepted. This is because tokenization simply has a higher measure of security. Since hackers can’t decipher a token, even in the case of an accidental breach, it is relatively state.
But there is one problem that both methods share. Whether you use tokenization or encryption, chances are that the sensitive data has still touched your systems. Which means if a hacker can get to the data before it’s tokenized or after it’s been de-tokenized, they won’t have any problems stealing that information.
Luckily, tokenization has evolved to deal with this issue.
Next Gen Data Security: Data Aliasing
A recent innovation in tokenization as a form of data security is data aliasing. Data Aliasing essential works as a token, except the raw data never touches your systems. Your databases and vault only store the token. Not only is this entirely secure, but it takes you out of PCI DSS scope.
But you may be wondering where the original data goes?
Data aliasing providers, like Very Good Security, intercept the data before it touches your systems with a proxy. They then store the data in a secure vault, and your business receives the token. When you plan to transfer this data, they also work as a proxy to decode the data, while you still only need to send the token
Basically, you can use the aliased token as if it were the original data. But if a hacker tries to get their hands on it, the token will be worthless.
Similar to general tokenization, these tokens cannot be deciphered or reverse-engineered. So the sensitive data remains safe and the effects of any breach are instantly minimized.
But there’s also other benefits to this approach as well. Because data aliasing takes your systems out of PCI DSS scope, you can become compliant in as little as 7 days. You can also reduce compliance costs by up to 75%, since you will no longer need to invest in infrastructure, an internal data security team, software, and other compliance-related tasks.
So if you are trying to decide between encryption and tokenization, it may be worth it to focus on the future and use data aliasing to improve your data security. Not only will it be easier on your bottom line, but you’ll have peace of mind knowing that your system is secure.