It’s no coincidence that a botnet group has a dedicated alias: zombie army. It enslaves hundreds of internet-connected devices and commands them to perform nefarious activities. The fact that hackers turn the machines into zombies without owners’ knowledge makes botnets even more fearsome. As much as robotic armies resemble pure science fiction, it’s a reality we live in. Hence, what is a botnet? How can your devices become a part of a zombie army? And, most importantly, how to prevent yourself from falling victim?
What is a botnet?
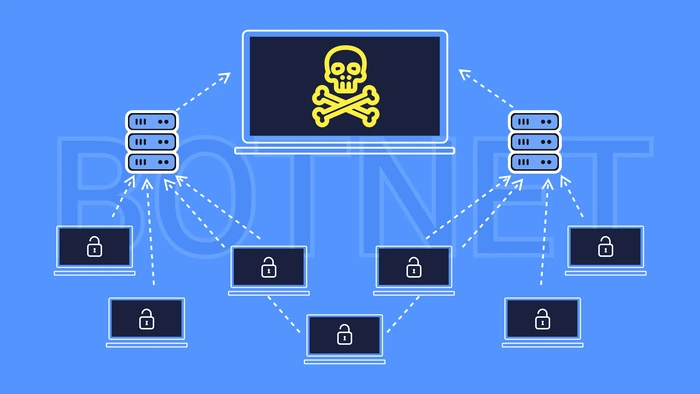
The term “botnet” is a combination of “robot” and “network.” A bot, short for “robot,” is malware that infects a device and carries out commands under the remote control. The “network” part stands for an army of internet-connected devices working together as a single unit. Hence, a botnet is a collection of infected and remotely controlled machines.
Botnets can range from a few hundred to millions of infected devices. They can enslave all IoT gadgets, such as routers, security cameras, or even smart refrigerators. If combined with wormable properties, the malware sends instructions to all the devices on a single network.
Controlling huge numbers of zombie computers allows attackers — called bot-herders — to perform large-scale malicious acts. They use botnets to perform various disruptive or criminal activities, such as:
- Sending vast amounts of spam emails
- Spreading malware
- Launching Distributed Denial of Service (DDoS) attacks
- Stealing credentials and financial information
- Spying on users and organizations
- Mining cryptocurrencies
How to detect botnet attacks?
Often, botnet attacks go undetected. Given the bot network’s size, a single device can require little bandwidth and continue to work normally. Since malware silently operates in the machine’s background, it doesn’t leave any footprint.
Still, there are some telltale signs that your device might be a part of a malicious network:
- Frequent device crashes without a clear reason.
- Slower internet connection and performance in general.
- Programs that worked seamlessly load slowly, crash, or malfunction.
- Ad pop-ups flash on the screen, even outside your browser.
- Your family or friends receive emails or messages you did not send.
How to prevent botnet attacks?
The best way to defend against a botnet attack is to have proactive safety measures in place. Follow these tips to prevent your devices from joining a zombie army:
- Improve passwords for smart devices. Instead of leaving default credentials that are easy to crack, change them to unique, long passwords.
- Use a VPN. It encrypts and anonymizes your traffic, meaning that no hacker can steal your data. Also, a VPN for PC might have features that prevent you from visiting malicious websites, including those possibly infected with botnet malware.
- Keep everything up to date. As previously discussed, botnets can use unpatched vulnerabilities to spread from device to device. Therefore, the first defense line is to keep all your systems — both software and hardware — updated.
- Always use antivirus or firewalls. A robust security suite can protect your device against malware infections.
- Be wary of social engineering techniques and spam. Always remain vigilant about any suspicious attachments or unusual links in emails or messages. Verify the identity of whoever contacted you, especially if you didn’t expect it.
- Update security settings for IoT. People having access to your network’s activity makes botnet attacks easy to execute. Thus, check all possible privacy and security settings on anything that connects device-to-device or to the internet.
How does botnet work?
There are several different methods of how the attacking party creates bot networks:
- Distributing spam campaigns via email, social media networks, or chat apps. The key purpose is to spew spam at high volume and deliver malicious payloads for thousands of targets. However, the attacking party can also use social engineering techniques to trick victims into opening malware-infected attachments or links.
- Exploiting flaws of unsecured devices. In the case of IoT devices, bot-herders can take advantage of weak passwords and default credentials. Also, these devices rarely have any antivirus controls, making the malware infection easier and detection harder. Botnets rely on unpatched IoT devices since these are often difficult or impossible to patch.
- Drive-by downloads. Attackers can exploit vulnerabilities in browsers, add-ons, or plug-ins and inject malicious elements into them. Drive-by downloads are especially tricky — they don’t require any action on your part. It can occur during browsing or mundane email click.
Conclusion
Botnet attacks link a group of devices together to do hackers’ bidding. So, users are in danger of getting targeted by such devices. However, it is also a risk that your device becomes a part of this malicious activity. Therefore, your device might be suspected of performing unlawful activities.
In the end, you should protect your devices and networks to avoid both situations. It should be manageable if you have necessary security measures. Furthermore, keep an eye on your systems to detect suspicious activities in time.